What are the Security Risks of Cloud Computing and How to Avoid Them
Updated 07 Jul 2023
15 Min
1913 Views
Cloud computing brings many benefits both for digital startups and large businesses. It enables cost reduction, performance optimization, and enhanced business agility. However, cloud security risks are the primary concern to successful operation. Once you handle them, you will be able to make the most of the secure cloud environment.
We’ll cover the most common cloud computing security risks and how to mitigate them to take advantage of cloud solutions. You’ll also know why to consider security risks backed with infamous worldwide cyber attack statistics.
What is Cloud Computing Security and Where Is It Needed?
Before delving deeper into cloud computing security risks, let’s look at the notion of cloud computing. It will assist you in better navigating the subject.
Cloud computing is a way of providing on-demand computing services over the Internet on a pay-as-you-go basis. Simply put, rather than managing files and services on a local storage device, you can do the same over the network in a cost-efficient way. It’s used for a variety of use cases such as data backup, disaster recovery, virtual desktops, big data analytics, and more.
However, just because all the workloads are in a cloud doesn’t mean it’s safe. Most major cloud service providers offer standard cyber security tools, but they do not always cover all the enterprise's security needs. That’s why it’s better to appeal to an experienced vendor like Cleveroad that will help you build a secure and scalable cloud-based solution, fitting your business needs.
Even though there are different ways to mitigate cloud technology security risks (depending on the type of the threats), we would like to share with you the best practices that all companies should follow to ensure IT system security.
- DevOps process. Reliable DevOps services will help you enhance code quality, eliminate exploits and vulnerabilities, and accelerate software development and features deployment.
- Automated operations. Even the most experienced cloud-based developers cannot keep up with the increasing volume and pace of security threats. Thus, it’s better to implement automation software solutions to remove routine tasks and speed up the development process.
- Unified control. Consider incorporating a centralized management system with open integration fabric for better controlling all interlinked processes. It will streamline the workflows and simplify the system monitoring by joining the parts together.
- Rules compliance. You need to create privacy and compliance policies that describe how employees interact and pass data. In addition, you have to make a framework of governance that determines authority and distributes responsibilities within the organization.
- Regular audit. It’s crucial to check your IT system in case of malware attacks. There are three main areas that should be constantly audited: security in cloud servers, access to the audit reports, and internal level of control of cloud vendors.
- Integration with blockchain technology. Blockchain in cloud computing will help you avoid data breach due to information encryption and strong databases protection.
Learn how IT Managed Service can help you handle your cloud IT infrastructure
It is also worth mentioning that the cybersecurity software tools are different depending on the industry. Hence, proper research and planning are required to apply the best security software aligning with your business needs. Let’s consider what sectors benefit most from the security software.
Healthcare industry
Health organizations deal with many sensitive personal data, including diagnosis, identity, addresses, and financial status.That’s why they face challenges complying with increased cyber risks and data breaches. According to the 2021 Verison report, there were 655 incidents, 472 with confirmed data leakage.
A large-scale attack on a healthcare establishment may stop its entire operations for health-related services. Therefore, it is the core reason hospitals incorporate security software in their system to guarantee protection from cybercriminals. First, however, healthcare providers need to ensure that integrated software is regularly upgraded and keep up with the latest versions.
Finance and banking industry
The financial industry is a tidbit for hackers. According to the last report, 89% of cyber attacks were financially motivated. Financial institutions gather a massive amount of confidential data regarding their clients’ financial status. Bank account details, addresses, business clients’ identities, and other valuable information are targeted by cyber criminals. Therefore businesses belonging to the financial sector need to implement advanced security software to get the strictest control over their data, restrict user access, and increase employees' security data awareness.
Retail industry
The majority of transactions in the online shopping industry are carried out through the internet. It makes the retail sector vulnerable to malicious activities. Retailers have access to a mass of sensitive information about their clients, who often employ repeated login details for their accounts.
With access to clients’ databases, hackers can send phishing emails and ask for personal details, attach malicious links, or add malware that can break down a customer’s PC. As a result, deciding to build an online marketplace, you must create the impregnable security barrier of your business since monetary loss and brand reputation will be at stake.
Manufacturing
Manufacturing companies are no strangers to cybercrimes. Manufacturing is now more complex, merging equipment, software, and smart devices. As a result, expanded capabilities lead to frequent hackers’ attacks, affecting a company's overall risk posture more power than ever before. Additionally, the manufacturing security team is less experienced in combating rising cyber attacks and sophisticated methods that are applied. Finally, as environments become more digitized, it gets harder to determine and understand the risks that go with these networks.
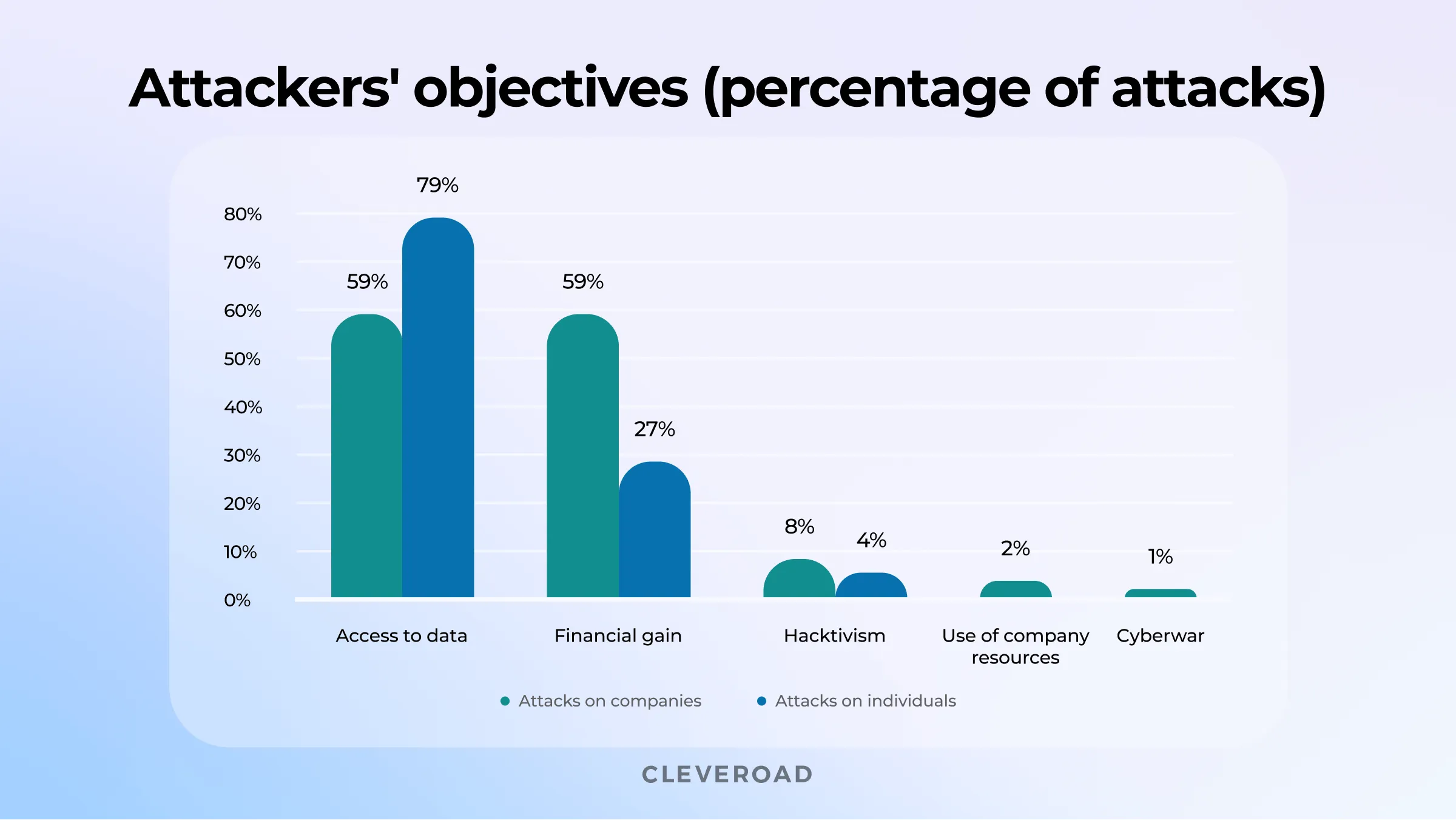
Hackers' motivates
Why You Have To Consider Cloud Computing Security Risks
Regardless of the great benefits, saving your workloads to a publicly available cloud leads to new data security risks, which may cost you a hundred of thousand dollars. Thus, if you’re planning to migrate to the cloud, it’s critical to consider cloud security risks, and here’s why:
- About 18 billion records of confidential data were breached in 2021 due to malicious attacks.
- About 60% of small businesses go out of business within six months due to cyber attacks.
- Misconfigured clouds were a leading cause of breaches.
- Approximately 1 in 4 Americans won’t do business with data-breached companies.
- The average cost of cyber attacks to small companies is $25,612.
- Remote work model adds a 238% increase in global cyberattack volume.
- The average cost of a data breach among organizations surveyed reached $4.24 million per incident in 2021 compared to $3,86 million in 2020. The highest cost of data breach of $9,23 million in the healthcare sector.
- About 70% of fraudulent transactions accounted for mobile devices.
These numbers indicate that cyber attacks are only getting worse, so it’s critical to take precautions today to secure your IT system from possible threats.
Moreover, the growing popularity of the work-from-home model adds to the increased number of cyber attacks. The study revealed that 47% of companies moved 61-80% of their employees home. As a result, malicious users get expanded opportunities for cyber violence due to the extensive use of remote work tools such as RDP (Remote Desktop Protocol). Let’s take a quick brief on the most common remote work cyber security risks.
Using personal devices for work
This security concern is connected with BYOD (Bring Your Own Device) usage. The term refers to a policy of permitting employees to use a single device for both work and personal purposes. The biggest concern businesses face is the risk of compromising enterprise data due to using unsanctioned devices. To avoid this issue, a BYOD policy should be adopted.
Phishing schemes
Phishing schemes aim to collect sensitive data using deceptive emails and websites. The attackers impersonate a trusted entity, often a real person or a company, to trick a victim into submitting private login credentials or confidential data, which can be used to access the account, steal privileged information, carry out identity fraud, etc. The best way is to implement a security awareness training program.
Insecure home Wi-Fi
It’s common to think of workforce laptops’ security, while the safety of home router’s software is often ignored. However, routers that aren't upgraded won't have security gaps fixed, which can result in data breach risks over time. In addition, many people don’t have a firewall to ensure their home's network security. To handle this issue, the router software must be updated regularly. Besides, some routers provide different encryption features that can be activated. Finally, for those specialists who deal with a lot of sensitive data, a security gateway should be provided.
Passwords
Despite the introduction of cyber security software, human errors make a move when employees shield their accounts with easy-to-crack passwords. Hackers employ a bunch of measures to break passwords. Moreover, sometimes they write code created to continuously attempt to break a password by picking out various combinations. After a while, the bot can likely crack users’ accounts. The best way is to implement a password policy. Passphrases and bans on employing personal data and repeat passwords for logins are recommended.
Unencrypted file sharing
Your employees share a vast amount of confidential data daily: from clients’ personal information to financial data and more. Thus, it’s not sufficient just to encrypt information stored on the network; it also needs to be encrypted while transitioning from one location to another. If third parties capture sensitive data, it can result in identity fraud, thefts, malicious attacks, etc.
What are the Security Risks of Cloud Computing?
There are several security risks to consider when migrating to the cloud. Here are the top ten dangers of cloud computing your company should be aware of to prevent possible risks in the future fast.
Poor Access Management
Access management is number one on the list of cloud computing security risks. Having access to the information is key to everything. That’s why hackers are attacking it so much.
For example, in May 2021, the Colonial Pipeline, one of the largest oil and gas companies in the United States, experienced 100 gigabytes of data stolen within a two-hour window. The cause was connected with poor crisis management, poor information campaign, and the hackers' proficiency. As a result, many computer systems, including billing and accounting, were affected due to security flaws.
So how to handle this problem to not go over the Colonial Pipeline painful experience? Here are some preventive steps:
- Use multi-factor authentication. Apart from a regular password, the user receives a single-use key on their device. In case of a break-in attempt, the users get warning notifications.
- Apply a separate layout for access management on the service side. This layout means that information is available for certain types of users. For instance, the marketing department doesn't require access to financial department data and vice versa.
Data Loss
Data loss is a threat that is hard to predict and even harder to deal with. The reasons for data loss vary from loss of access to data deletion and data modifications.
One of the well-known examples of data loss is the MySpace debacle.The largest social platform from 2005 to early 2009, MySpace has experienced uploaded content getting lost, including media uploads like images and music. What happened? During the migration to the cloud, it came out that a considerable amount of customer data got lost due to information corruption. Unfortunately, since the company wasn't doing frequent data backups, the data couldn't have been restored.
How to avoid this issue? Here are some preventive measures:
- Backups. Data backups are the best way of preventing data loss from happening. You need to calendar for the operation and define what type of information is permitted for backups and what is not. The process can be automated by using data loss prevention software.
- Geodiversity. The situation when the physical location of the cloud servers in data centers is dispersed and not subject to a particular spot. This feature is allowed to handle the aftermath of natural disasters and power cuts.
Insecure API
Weak API is another widespread cloud threat. Application User Interface (aka API) is the core instrument applied to operate the software within the cloud infrastructure. This process encompasses internal use by the enterprise’s employees and external use by customers via digital products like mobile or web apps. The security of the exterior side is crucial since the service is responsible for data transmission and submitting all kinds of analytics. The accessibility of API makes it vulnerable to cyberattacks.
The most well-known example of API vulnerabilities is the Cambridge Analytica scandal. Facebook API had rich access to user data, and Cambridge Analytica employed it for its own gain.
How to prevent problems with API? Here are what can be done:
- Perform penetration testing that imitates an external attack targeting definite API endpoints, breaking the security and accessing the organization's internal data.
- Provide general software security audits
- Apply SSL (Secure Socket Layer) encryption for data transmitting.
- Use multi-factor authentication to block unauthorized access due to security breaches.
Data Breach
A data breach is an accident where third-party users access and extract information. It leads to data leaks when the information is located where it is not supposed to be. Private data is accessible to the public, but commonly, it is sold to the parties concerned held for ransom.
The most infamous example of a data breach happened in 2017 in Equifax, a US-based credit reporting agency. The company lost confidential data of over 143 million clients because of software modernization negligence. Equifax’s software engineers hadn’t upgraded the system to fix the detected vulnerability. In 2021, similar attacks didn’t stop. The ReproSource, a clinical laboratory for fertility specialists, suffered from a cyber attack, resulting in 350,000 patients' data theft. According to the initial report, the data wasn’t encrypted properly.
How to prevent data breaches from happening? You can consider the following practices:
- Data-at-Rest Encryption. Data-at-rest is a type of information stored in the system but not actively employed on various devices. This process relates to logs, databases, etc.
- A network perimeter firewall between a private and public network that protects the system against unwanted traffic.
- Internal firewall to track authorized traffic and identify anomalies.
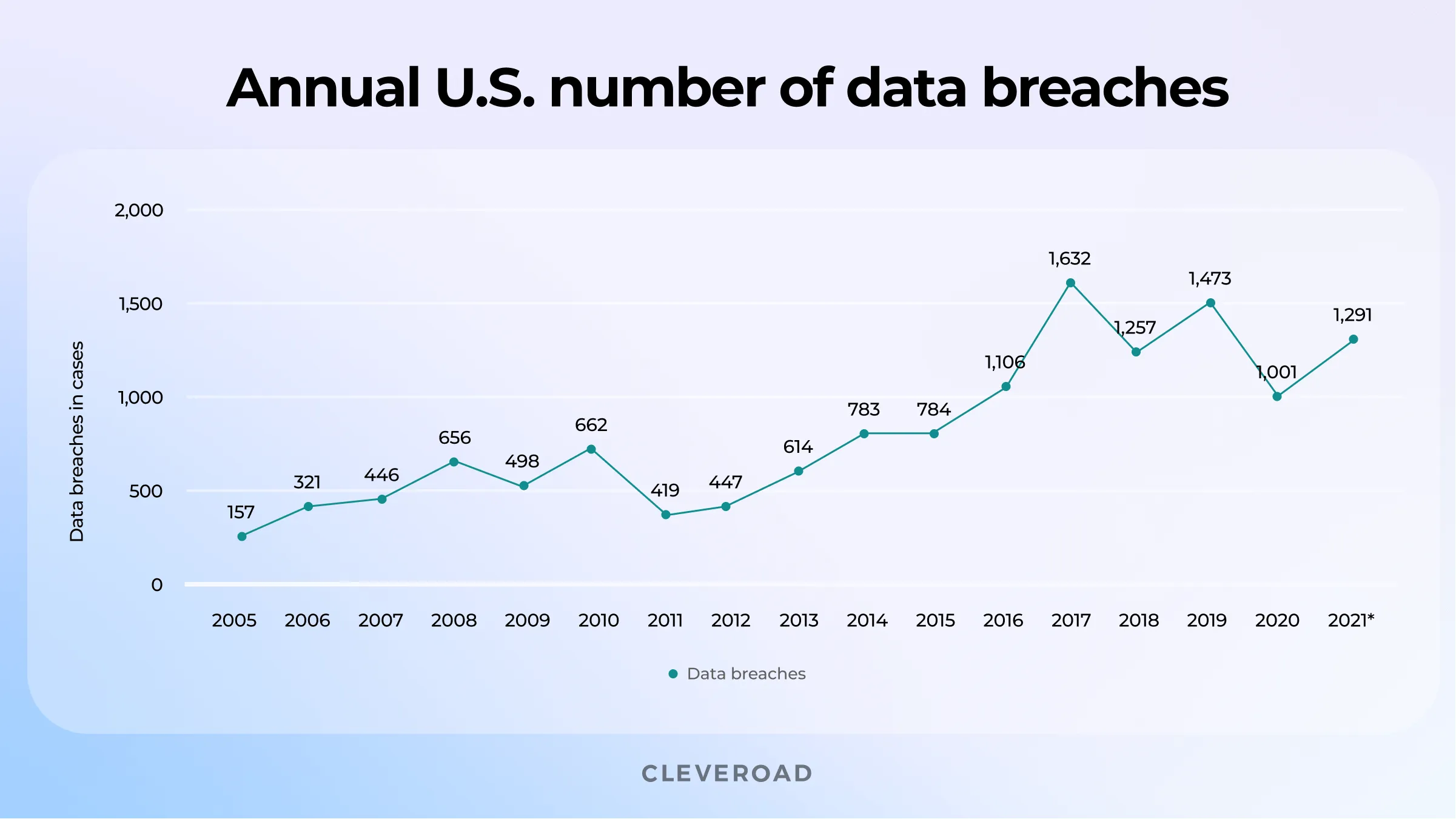
Annual number of data breaches in the United States from 2005 to 2021
Cloud Misconfiguration
Cloud misconfiguration is when an enterprise has not set up its cloud system correctly, making it vulnerable to hacking. Commonly, it happens because of default cloud security settings, mismatched access management, and deformed data access.
A good illustration of cloud misconfiguration in action is the Estee Lauder company failure. More than 440 million records that enclosed clients’ email and audit, error, CMS, middleware, and production logs were exposed.
Here’s how to handle it:
- Double-check cloud security configurations before setting up a specific cloud server. This step is often neglected for the sake of more essential things locating stuff into the storage without considering the safety measure.
- Apply specialized tools to control security configurations. There are different 3rd-party tools like CloudSploit that enable security configuration verifications on a schedule and detection of possible issues in advance.
DoS Attack
A denial-of-service attack (DoS) aims at preventing users from getting into the system or interrupting their workflow. How does it work? During a DoS attack, the system assets are depleted. Lack of resources for scalability provokes different speed and stability issues throughout the system. For instance, the application runs slow or doesn't load properly.
The Amazon Web Services attack is a notorious example of DoS attacks. The attack lasted for three days and peaked at an incredible 2.3 terabytes per second.
Here is how you can block DoS attacks:
- Using Intrusion Detection System. The system detects unusual traffic and gives warnings based on credentials and user behavioral factors.
- Blocking IP addresses that are seen as malicious sources helps you reduce the security risks.
- Adding Firewall Traffic Type Inspection features to be able to verify the source and target of incoming traffic and determine its nature with the help of IDS (intrusion detection system) tools.
Poor Due Diligence
Another reason leading to cloud security risks is extreme shortage of experienced specialists capable of ensuring security for cloud apps. Therefore, when dealing with service cloud providers like Amazon Web Service (AWS) or Microsoft Azure, it’s critical to conduct in-depth due diligence to ensure that your company is aware of the scope of work needed to migrate to the cloud successfully.
However, organizations don't understand how much work is involved in the transition in many cases, and security measures are often ignored.
To manage this issue, it’s better to cooperate with certified cloud security professionals with a thorough understanding of software protection mechanisms. For example, you can hire our AWS accredited specialist that helps you deliver quality services with security at heart.
Malware Infections
By transferring a significant amount of private data to the internet-connected cloud environment, enterprises are becoming vulnerable to additional cyber threats. Malware attacks are a common risk in cloud security, with studies demonstrating that nearly 90% of the companies that fail to manage public cloud use will inappropriately share confidential information by 2025.
As malicious users become more sophisticated in their attack delivery methods, enterprises must be aware of the fast-changing threat landscape.
How to defend against malware? Here are some practical steps to take:
- Keep your computer and software updated. Install updates once they become available for your operating system. These updates often contain fixes that can enhance the system’s security. As for the computer’s software, it should be kept up with the latest versions.
- Restrict your file-sharing. If you use special websites and applications for file exchanging, watch out for malware. Malware can often be cloaked as a famous movie or program.
- Use antivirus software. Antivirus programs allow you to detect malware early and keep it from spreading.
Discover how to build a cloud-based app in our ultimate guide
Lack of Operation Visibility
When moving workloads and resources to the cloud, companies encounter restricted visibility into network operations. It is because the responsibility for system management shifts toward the cloud service provider. The level of commitment varied depending on the vendor. Thus, organizations must be able to control their network infrastructure without applying network-based monitoring and logging.
Here are some ideas on how to enhance cloud visibility:
- Add probes and tracing. Consider inserting app performance monitoring probes into the code. Embed probes at specific points where it’s critical to establish visibility.
- Centralized monitoring. When data is split, it becomes harder to interpret it. Centralized monitoring gathers monitoring information and saves historical data for analysis in one place.
- Integrate AI and (ML) tools. Artificial intelligence and Machine learning enhance cloud visibility because it increases the speed and complexity of data interpretation. These technologies presume that operations staff can’t explain the available data and take proper action.
Compliance Violations
Inability to comply with regulatory standards is the last cloud computing risk on our list. Companies are constantly combating stringent requirements of various industry standards such as GDPR, HIPAA, PCI compliance process, etc. Therefore, the best way to guarantee ongoing compliance is by monitoring who has access to the information and how exactly they can deal with data. In this regard, user access control is a crucial measure for ensuring cloud security. For instance, you can apply a zero-trust security method, implying that no one can be trusted with open system access. Instead, the access provided depends on the employee's roles.
How Cleveroad Secures Cloud Software
Cleveroad is a software development company with deep practical expertise in creating and scaling cloud solutions. Since 2011 we have been assisting startups, SMBs, and enterprises in getting custom cloud-based software aligning with their needs and budget requirements. Our expertise covers finance, healthcare, e-commerce, logistics software development, education, and other business domains.
Benefits of cloud adoption with Cleveroad:
- Proven proficiency in cloud development and migration.
- Knowing the peculiarities of major cloud services, including Amazon Web Services, Microsoft Azure, and Google Cloud Platform.
- Software engineering teams consisting of secure-oriented, high-qualified, and certified professionals.
- A complimentary consultation with our Business Analysts about your project
- Non-disclosure agreement (NDA) signing per request.
- Innovative development approaches and cutting-edge tech stack.
Whether your business is a startup or a large enterprise, cloud security means everything. Cleveroad professionals are experienced in designing secure cloud computing infrastructure, and are ready to help you deliver high-end software ensuring all the security requirements.
Get a secure cloud solution
Contact our experts to build secure cloud-based software fitting your business needs
Cloud security risks implies malicious users, seek to exploit cloud service security vulnerabilities to steal sensitive data for ransom or other illegal purposes.
There are several security risks to consider when migrating to the cloud. The top-four dangers of cloud computing are data breach, poor access management, misconfigured cloud storage, and denial-of-service attack (DoS).
Every organization has its own cloud security policy in place. However, here are some best practices all companies should follow to ensure IT system security:
- Reliable DevOps services
- Automated operations
- Unified control
- Rules compliance
- Regular audit
Who owns the information owns the world. Regardless of the great benefits of cloud solutions, saving your workloads to a publicly available cloud leads to new data security risks, which may cost you both financial and businesses losses (brand reputation, customer base, etc.). Thus, in order to make the most of the secure cloud environment, it's crucial to cooperate with experienced vendor who will help you build and implement cloud adoption strategy.

Evgeniy Altynpara is a CTO and member of the Forbes Councils’ community of tech professionals. He is an expert in software development and technological entrepreneurship and has 10+years of experience in digital transformation consulting in Healthcare, FinTech, Supply Chain and Logistics
Give us your impressions about this article
Give us your impressions about this article
Comments
1 commentsValuable information and excellent design you got here! I would like to thank you for sharing your thoughts and time into the stuff you post!! Thumbs up