New Authentication Methods That Shape the Future of Mobile Security
Updated 26 Aug 2023
10 Min
3233 Views
In Maslow's hierarchy of needs, safety comes second after physiological requirements. It indicates an extreme importance of this aspect and shows that people cannot proceed to the repletion of wants on a higher level if they feel insecure. Protection is essential for each sphere of human activity.
With the rapid leaps in technology, the demands of this factor also grow. Just a few years ago, the users were content with passwords set on their apps. Now, this way of authentication smells rather fishy.
According to the Gartners research, nearly 95% of web apps face hacking attacks because of stolen passwords. It proves that a unique set of numbers can not guarantee a reliable data protection. Bearing this in mind, many companies started working on more advanced methods of establishing security. Lets review some of them and find out which ways they are reshaping the future of app authentication.
User authentication methods
Below, I have listed the most popular authentication methods that are used when providing proper mobile app development services.
Digital certificate
A digital certificate is an electronic document released by the Certification authority. It confirms the accessory of the public key or it's attributes to the owner. Digital certificates contain identifying information. Because it is issued by the specialized, trusted organizations, it can be easily verified.
Digital certificates are obliged to include the following components:
- Certificate holders name
- Certificate serial number
- Certificate expiration date
- A copy of the public key that belongs to the certificate holder
- Electronic signature of the authority that has produced the certificate
The public key is needed to encrypt the messages. The electronic signature serves for verifying data consistency. For this purpose, each browser and the operating system have a list of trusted authorities and can easily identify whether a given signature belongs to one of them.
Smart card
Smart card is a reliable way to store the private key of the owner. It also serves for entering this key during the authorization. Basically, the smart card is a security chip that integrates into a credit card or SD memory. You can either insert it into the device directly or use a wireless connection so that the device could read the chips information.
Once it is done, the encryption algorithms quickly interpret the smart cards data. As a result, the user gets a fast and accurate access to the device, program, or application.
Hardware key
Hardware key is a small physical device that generates a random password for a single use. This password remains valid for a very short period of time - usually, not longer than one minute. A cryptographic mechanism produces every unique set of characters in a logical sequence developed by a special algorithm.
To use a one-time code provided by the hardware key, the user needs to enter his or her own password followed by this string.
Do you want to create a secure Android application? We are telling you how to do this in our article: What keeps your applications secure
Biometrics
Biometrics is a great way to authorize users without involving any passwords or other kinds of authentication. This method of identity verification is based on the data that is unique to each individual. It unlocks the system with the help of fingerprints, voice patterns, iris scans, handwritten signatures, etc.
Biometrics may be used as the only way of authentication or as one of the components of multi-factor verification. In the latter case, a password or a token may act as an additional element to log into the program or application or enable the device.
Proximity
Proximity involves unlocking a device or a program when certain conditions are met. Such conditions may include the geographical factor or presence of a specific device. For instance, a mobile phone may stay unlocked when it communicates with Bluetooth headgear or when the user is at home or in any other specific area.
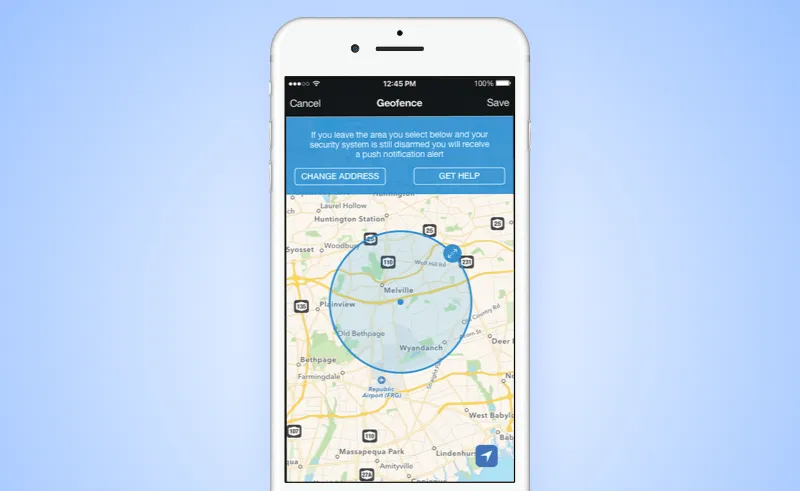
Proximity authentication based on geofencing
The technical background of the proximity authentication is organized by the RFID tag readers. They open access to mobile devices that get through the security checkpoint and block those that do not meet the required conditions.
Security authentication technologies
Lets review a few services that can be used for mobile and web solutions to build the lookout security.
KodeKey
KodeKey enables the authentication process based on the biometric data. KodeKey communicates that the user does not need to create a password, because he or she has everything for fail-safe entry, namely a phone and unique personal data.
In spite of the fact that biometric authentication is considered to be quite an expensive technology, the KodeKey assumes that the majority of users own devices with fingerprint scanners and other progressive secure elements already.
The KodeKey server stores the information about each user's account and links it with a particular phone number or PIN. Specially designed web-based API guaranties an effortless integration of the authentication service into any website. You can also refer to the special WordPress plugin to make the integration even smoother.
In general, the scheme of KodeKey authorization may be described as follows:
- The user enters his phone number or PIN in the login field
- The KodeKey app receives a notification about the attempt to enter the system
- The KodeKey app responds with the request to authenticate the users identity by scanning his or her fingerprint
LaunchKey
LaunchKey offers different ways of identity verification including time-honored passwords, authentication in a real time mode, and two-factor authorisation.
You can access the LaunchKey engine via the public API, on-premises, or in the cloud. The system is organized so that personal records are never kept in the LaunchKey engine but stored on the users devices.
Thanks to the platform flexibility that provides an opportunity to build app security with the help of various combinations of authentication methods, you can create your own protective mechanism.
For instance, to protect corporate data, you might initiate a person's identity along with checking their physical location at the attempt to access the system. It will make a background for building two-factor authentication based on biometric data and geofencing. If your scope of activity extends to monetary operations it would be reasonable to perform a user authentication at each transaction.
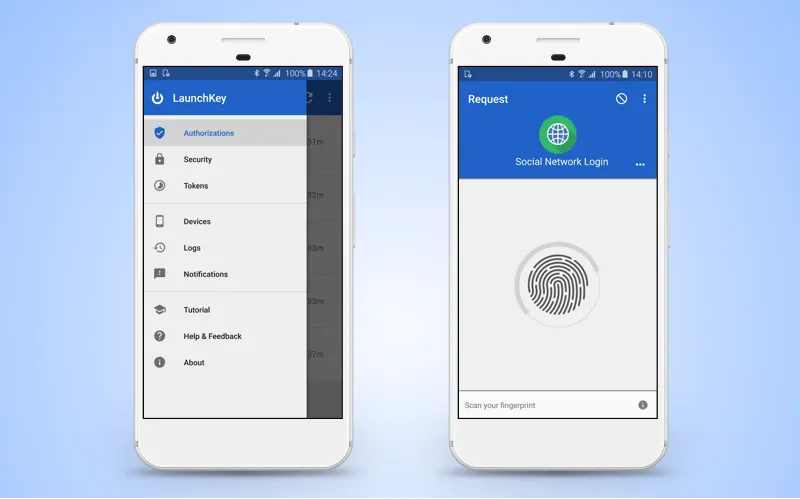
Entering the system with the help of service powered by LaunchKey technology
Clef
Clef presents itself as a password-less service for organizing a secure login. The involved instruments include a smartphone camera and an asymmetric key. Thanks to them, the verification confirms a secure combination of the randomly generated images and a unique key.
To user obtains a private key when he or she creates a Clef account and installs an app on their phone. The private key is stored on the users device. At the same time, the public key is sent to the Clef server.
When the user logs into the service that is integrated with the Clef mechanism, he or she sees a randomly generated image in a browser. The user enters the Clef app and directs the phone to the monitor screen. The application identifies the picture, encrypts it with the users private key, and passes it to the Clef server.
The server sees that a particular user sends a particular image encrypted with the correct key. Based on this data, it concludes that the input was performed by the right user. The server passes this information to the site. The latter allows the user in.
Miracl
Miracl replaces traditional passwords with the unique combination of PIN and token that builds a special M-pin cryptographic application. A set of numbers created this way deploys an authentication protocol with a zero-knowledge proof on it's server.
The server is not aware of any personal data, passwords, or other sensitive information related to the user. However, it keeps a key that consists of two parts. Each part is stored on a separate server. The first one is an app server, the second - Miracl server.
M-pin
M-pin serves both web and mobile solutions. In the first case, you integrate a piece of JavaScript code and the library into your website. In the second - you control the access to the personal account via a browser using a mobile app.
During registration with the service that works together with M-pin, the user attaches a specific device or a desktop browser to his or her account and adjusts a PIN. As a result, the selected device receives a special token that you cant log in without.
YubiKey Neo
YubiKey Neo is a successor of the famous security authentication technology by Yubico with the use of physical USB keys. The YubiKey devices have seen heavy use among such tech giants as Google, Github, and Dropbox.
Currently, the Yubico developers are working on an authentication system for the next generation. It is based on the innovative physical key powered by NFC technology. They key represents the second factor of two-step verification on mobile devices. To use the key, the user needs to put it to the back of his or her phone and press the button in order to generate a unique string of numbers.
YubiKey Neo security authentication technology
YubiKey Neo can also be used as a familiar USB key. It means that you can plug it into the USB port of a desktop computer when logging in. Since the key does not save any personal information about the user, it is necessary to know the account credentials to enter the system.
What is the best approach to set up network security?
The above technologies are definitely a leap forward in a way of implementing a high level of security. Yet, it may be rather problematical to decide on one service or another for a non-specialist in a mobile development area. To facilitate your choice, we would like to list some pros and cons of mobile protection methods based on our own experience.
Security is more than important for healthcare mobile application development. Learn how to ensure it in our latest guide
In most cases, we have been dealing with two-factor authentication, where the first factor is login/password and the second - one of the solutions below:
Validation via SMS
Pros:
- Easy to implement
Cons:
- The sim card can be easily falsified
- The user needs to spend money to receive the SMS
- SMS may fail to reach the destination in some countries
- A phone with a sim card is required
Validation by fingerprint
Pros:
- Easy to implement
- The system stores the finger scan on it's own
Cons:
- Only available on devices with a finger scanner
- A phone supporting this technology is required
Validation by PIN
Pros:
- Easy to implement
- PIN is stored locally and may be different on different devices
Cons:
- There are some special aspects for storing PIN
- Additional services may be required
Validation by the Smart Card or Proximity
Pros:
- High level of protection
- There is no way to log in without the necessary cards and / or devices
Cons:
- The availability of these cards and devices is a must
- You should make significant investments to get the necessary equipment
- The cards and devices may be lost or get broken
- A phone or other extra means are required
The most common options are SMS and PIN validation. The other approaches are more expensive with regard to the number of hours needed for implementation.
Biometric authentication by face and eye is difficult to implement. During a person's verification, a large data inaccuracy may occur. Besides, this technology has poor performance on mobile devices.
Digital Certificate is difficult to use for the average user as he or she may lose or forget the password. To restore this certificate without the password is impossible unless you keep it somewhere in the system. The latter approach seems to be insecure itself.
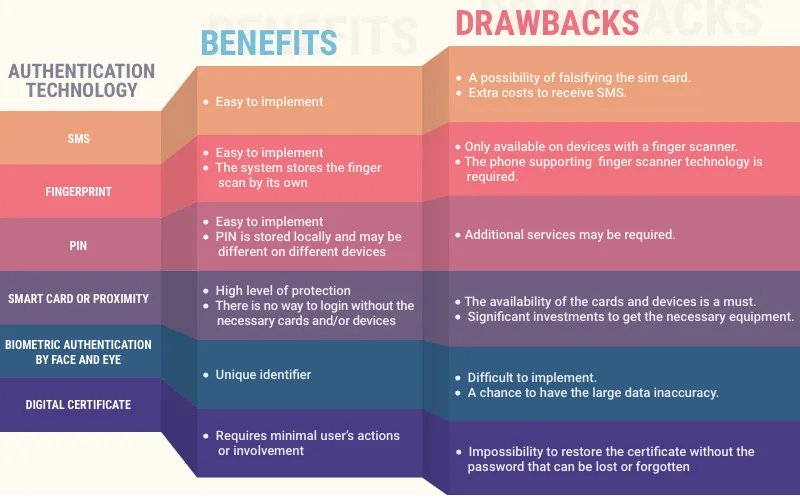
Pros and cons of different authentication types
As you can see, there are a variety of technologies that provide authentication security. To make the right choice, you should take into account the specifics of your business. For any further questions concerning this subject feel free to contact us. We will be glad to provide an expert help and advice on the best security mechanisms that will fit your app the best way.

Evgeniy Altynpara is a CTO and member of the Forbes Councils’ community of tech professionals. He is an expert in software development and technological entrepreneurship and has 10+years of experience in digital transformation consulting in Healthcare, FinTech, Supply Chain and Logistics
Give us your impressions about this article
Give us your impressions about this article